A few years ago, my friend got a call from “her bank.” The voice on the other end was polite, well-spoken, and oddly familiar. It was asking about a flagged transaction, reading out her account details, and even confirming her date of birth. Something didn’t feel right, so she hung up.
Two hours later, her savings account was emptied.
That’s identity theft in 2025. It’s no longer just about a stolen wallet or a forged signature. It’s a well-oiled machine, operating quietly, often invisibly, until the damage is done. And the scary part? The rise isn’t just steady — it’s accelerating.
Why? That’s the messy part.
The Breach Problem Nobody’s Fixing
Let’s start with the obvious: data breaches are now part of daily life. They barely make headlines unless they’re spectacular in size. We shrug at the news of “millions of records exposed,” the way we might sigh about another traffic jam.
When Equifax lost the personal data of 140 million people back in 2017, it felt like a wake-up call. Spoiler: nobody woke up. Since then, breaches have gotten bigger, more frequent, and more intimate. It’s not just names and addresses anymore — it’s ID numbers, financial details, biometrics.
And here’s the dirty truth: once your data is stolen, it’s never gone. It’s copied, traded, bundled, and resold like old vinyl records in a flea market. Even if a breach only coughs up half your details, a fraudster can stitch together the rest from other leaks.
We’ve Become Our Own Security Holes
The second culprit? Us.
We overshare. Constantly. Birthdays, anniversaries, where we had dinner last night. We post old school photos with our best friends (hello, maiden names). We livestream from airports, effectively telling the world, “Hey, I’m not home right now, and here’s my location!”
You can’t really blame people for being social — the whole internet is designed to make us share. But the effect is that personal data has become cheap, plentiful, and easy to mine.
The AI Twist No One Saw Coming
AI has been billed as our great fraud-fighting ally — and to be fair, it is, in many cases. But tools like generative AI have also supercharged the bad guys.
What once took skill — forging a signature, mimicking a voice — can now be done in minutes. A voice clone needs maybe 30 seconds of clean audio. That’s less than what you’ll find in a single Instagram Story.
And it’s not just famous people being targeted. Ordinary folks get voice calls from “relatives” asking for urgent money, fake videos designed to manipulate them, or documents so realistic even seasoned bankers get fooled.
Verification Systems That Belong in the 90s
Here’s something nobody likes to admit: a lot of our identity theft verification processes are laughably outdated.
Banks still ask for scanned ID copies over email. Some employers still check résumés without actually verifying employment histories. And in many places, your “proof of address” can be a paper bill anyone with a printer could forge.
The problem is patchy adoption. One city might require biometric checks for a service, another accepts paper forms. Fraudsters know exactly where to strike.
Fast Transactions, Slow Realization
The internet’s obsession with speed is another problem. Instant account openings, instant loans, instant everything — it’s great for legitimate users, but it also gives criminals a head start.
A scammer can open multiple accounts, shuffle money across borders, and disappear before the first fraud alert even triggers. And since the digital economy is global, your personal data could be exploited in a country you’ve never even visited.
Crime Has Scaled Like a Startup
If you think identity theft is mostly lone hackers in hoodies, think bigger.
Organized fraud networks now operate like proper companies — complete with HR departments, training manuals, even subscription models for stolen data. Some sell “fresh identity packs” every month, others run call centers that impersonate banks, tech support, or government offices.
Economic instability in certain regions has only made this worse. For some, fraud isn’t just a crime — it’s an industry.
The Human Factor
And of course, there’s us again. Weak passwords. Reusing the same login across 12 different sites. Clicking links in emails we “know” are probably suspicious but just want to check.
Phishing works not because people are stupid, but because people are human — distracted, stressed, rushing between meetings. Scammers know this. That’s why their messages are urgent, their calls are timed, and their stories believable enough to bypass suspicion.
The Blame Game
If you’re looking for a single villain, you won’t find one.
The identity theft boom is the messy intersection of:
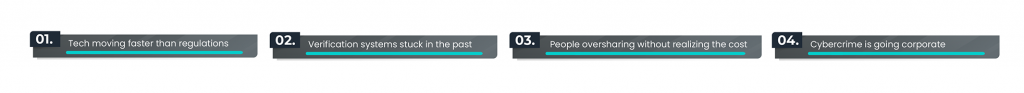
It’s a perfect storm. And storms don’t stop on their own.
So, What Now?
We can’t seal every leak, but we can make it harder for thieves to profit — and we can do it before they get inside the system.
One of the most effective ways is pre-onboarding background verification. Instead of waiting until fraud happens, organizations can screen individuals before granting access — whether it’s a new employee, a gig worker, a merchant partner, or even a high-value customer. This isn’t just about checking a name against a database; modern BGV can pull in criminal records, address, identity document authenticity, and even employment or education credentials.
When combined with AI-powered instant checks, the process becomes both thorough and fast. AI can scan a government-issued ID in seconds, compare a selfie to a photo database with facial recognition, and flag mismatches in real time. It can also cross-reference multiple data sources to detect inconsistencies that a human might miss — for example, a phone number linked to multiple unrelated identities, or an address used in known fraud cases.
This is crucial for industries like:
- Fintech & Banking, where instant loan approvals need to be balanced with fraud prevention.
- Gig Economy Platforms, where thousands of workers are onboarded daily and speed can’t come at the expense of safety.
- Real Estate & Co-living, where tenant verification can prevent fraudulent rentals.
Alongside these, the broader defense playbook should include:
- Multi-layered verification as a default, not a premium option.
- Digital literacy programs that explain how scams work, not just “what to avoid.”
- Stricter data security laws to hold companies accountable for breaches.
- Cross-industry collaboration so threat intelligence is shared, not siloed.
Protecting your identity isn’t about building an unbreakable fortress — it’s about creating enough locked doors, alarms, and tripwires that thieves move on to easier targets.




Leave a Reply